IAM Users vs Sub-Accounts vs Resource Groups: Choosing Your Cloud Admin

Imagine you're the CTO of a startup migrating to the cloud. Faced with challenges in team collaboration and cost management, you need to answer two key questions: How can team members safely share resources? How do you avoid confusion in financials and permissions?
In this case, the three core "administrators" of the cloud platform—IAM (Identity and Access Management) Users, Sub-Accounts, and Resource Groups—will be your best helpers.
Definitions and Explanations:
- IAM User: A permission entity (badge mechanism) that uses policies for authentication and authorization, similar to how employees use badges to access specific office areas (permission boundary control).
- Sub-Account: A resource isolation unit at the account level (independent subsidiary structure), with separate billing, resource pools, and quota systems, similar to how a subsidiary operates independently with default resource isolation.
- Resource Group: A business aggregation unit (cross-departmental project team), which gathers multi-account/user resources using tags and applies security policies, such as integrating cross-department resources for a temporary project group.
To help you understand the roles and uses of these features, we’ve provided three real-world scenarios that explain how to choose the most suitable collaboration method for your needs.
Scenario 1: Collaboration Challenges in a 5-Person Team
Background:
The team shares a master account but requires:
- Developers to manage servers but not view billing.
- Finance to only download invoices, and is not allowed to modify resources.
- All expenses to be billed to the master account.
- Strict separation between testing and production environments.
Solution: IAM User + Resource Group
- Create Identity Cards:
- The master account creates two IAM users:
- dev-engineer (Developer): Attached with ECSFullAccess policy (full server access).
- finance (Finance): Attached with BillingReadOnlyAccess policy (view-only billing access).
- The master account creates two IAM users:
- Define Resource Space:
- Create two resource groups:
- Prod-Env (Production Environment): Deploys the live order system.
- Test-Env (Testing Environment): Stores features not yet live.
- Create two resource groups:
- Precise Permission Matching:
- Developers can only operate servers within the Test-Env resource group.
- Finance can only view billing details, with other features hidden.
Outcome:
- Permissions as Access Control:
- IAM Users = Employee badge (decides building access).
- Resource Groups = Floor permissions (decides which rooms can be entered).
- Isolation and Sharing:The testing environment operates independently, but a shared log service can be accessed by both resource groups.
- Clear Cost Management:All expenses are billed to the master account.
Ideal Use Case:
- Teams of fewer than 10 members setting up rapid development/testing environments.
- Collaborative multi-project teams requiring shared basic services (e.g., databases, message queues).
- Compliance with ISO27001 and other audit requirements (easily trace actions via resource groups).
Scenario 2: "Independent Kingdoms" for a Corporate Group
Background:
A group has three main business (BU) units—e-commerce, logistics, and payment, and needs:
- Complete resource isolation for each business unit to avoid cascading errors.
- Independent cost accounting per BU.
- Self-management of internal permissions by each BU
Solution: Sub-Account
- Create Independent Kingdoms:
- The master account creates three sub-accounts:
- E-commerce : Manages product system with a dedicated department credit card.
- Logistics: Creates IAM users for transportation management.
- Payment : Sets up independent risk control policies.
- The master account creates three sub-accounts:
- Cross-Department Collaboration:
- The master account authorizes the Shared-DB resource group to the logistics sub-account for order data sharing.
- The payment sub-account temporarily acquires API access to the e-commerce system via RAM roles.
Outcome:
- Resource Physical Isolation:E-commerce server failures won’t affect logistics, like independent subsidiaries.
- Decentralized Financial Management:Each sub-account generates its own bill, making cost attribution clear.
- Autonomy with Oversight:Sub-accounts can create IAM users independently, but the master account retains auditing permissions.
Ideal Use Case:
- Group companies or divisions operating independently.
- SaaS platforms serving enterprise clients with data isolation requirements.
- Multinational businesses needing to comply with data sovereignty regulations (e.g., EU GDPR).
Feature Comparison: Three Keys for Different Locks
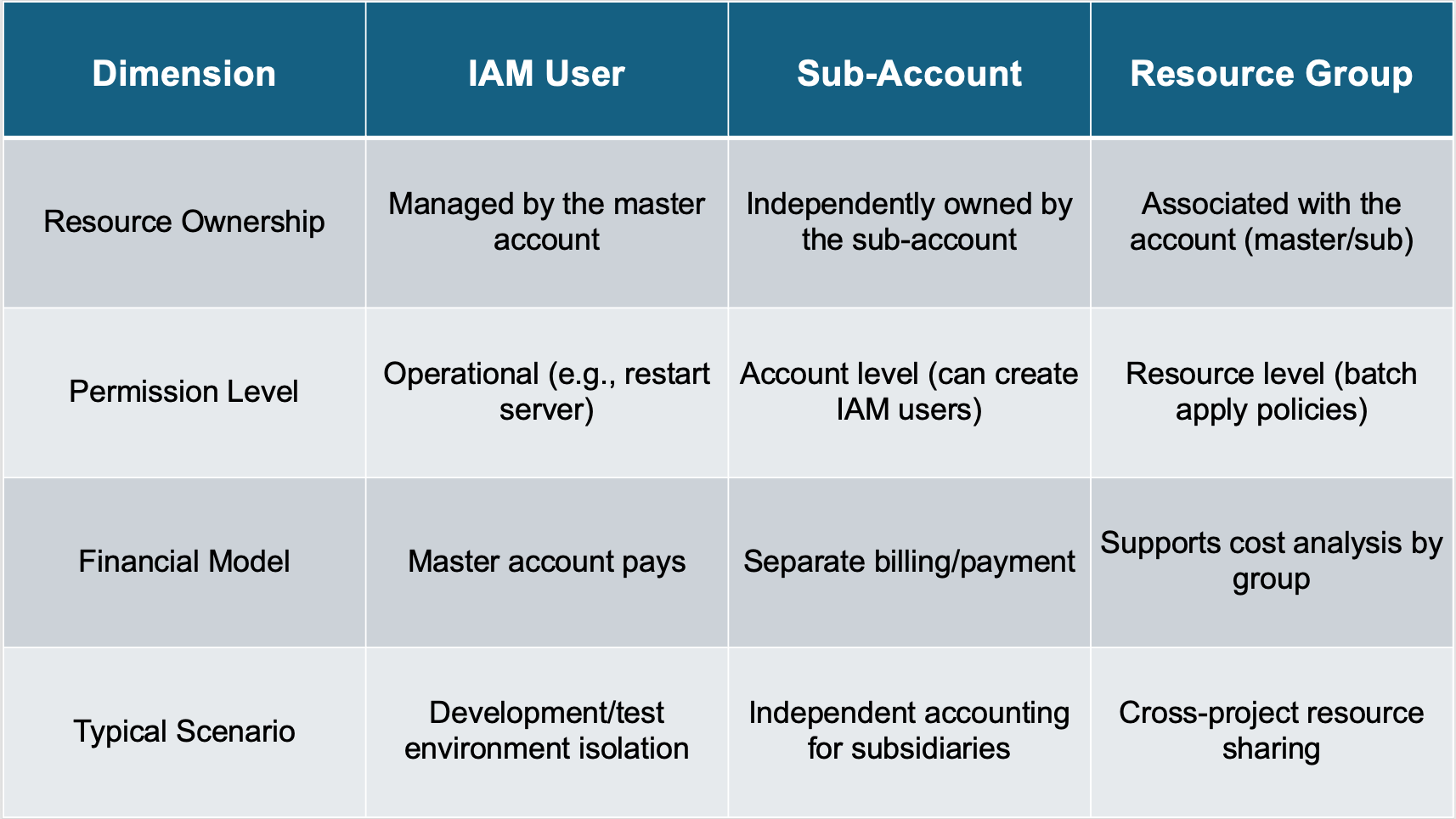
By combining IAM Users (fine-grained operations), Sub-Accounts (independent units), and Resource Groups (flexible grouping), enterprises can build a three-layer management system:
- Permission Funnel: Master account controls the overall environment → Sub-accounts manage autonomy → IAM users perform specific actions.
- Security Fortress: Sub-accounts physically isolate key business areas, while resource groups logically separate sensitive data.
- Cost Dashboard: Analyze spending by resource group, and use sub-accounts for departmental cost assessments.
In the future, as cloud platforms roll out intelligent policy recommendation features, these three tools will function like an automated driving system, optimizing permission configurations for a truly "hands-off" security management experience.
Bitdeer AI User Management
At Bitdeer AI, we provide all the above user management options, including IAM Users (fine-grained permissions), Sub-Accounts (independent management), and Resource Groups (dynamic resource allocation).
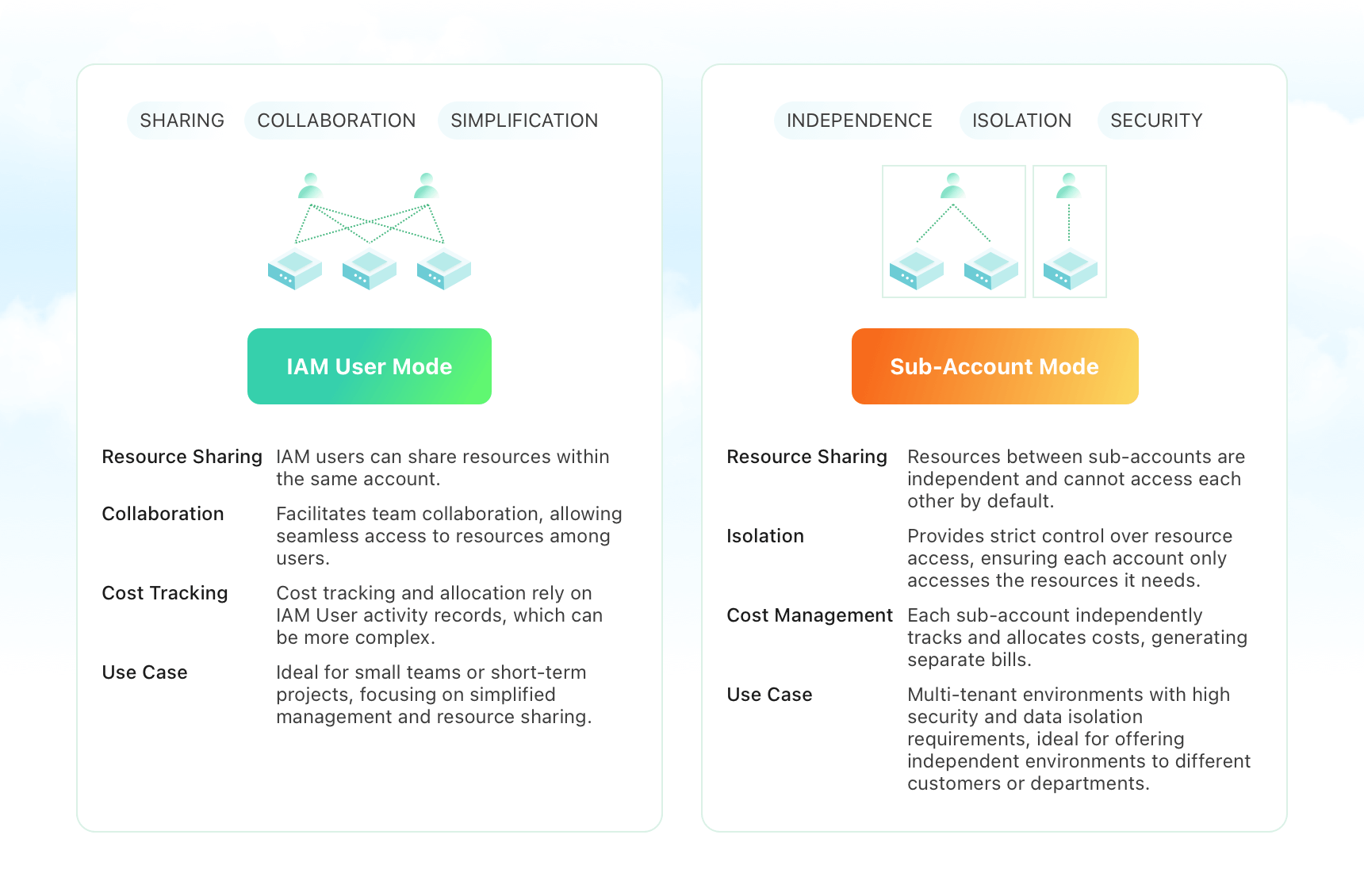
IAM Users allow you to finely control the permissions of each user as needed, ensuring security and compliance. The Sub-Account feature provides fully independent management spaces, ideal for team or department-level operations. Resource Groups help you group resources as needed, optimizing management and usage efficiency. These features ensure the platform's high flexibility and scalability to meet the needs of users of all sizes. However, please note that once you choose either IAM or Sub-Account mode, the decision is irreversible, so please select the method based on your business requirements carefully.
If you have any questions regarding the setup of IAM users or the management of sub-accounts, please feel free to contact us. Our team is ready to assist you in optimizing your cloud access and ensuring a smooth and secure experience. For further support please contact: [email protected].